Symantec Cyber Security Services
Our security services
Our Symantec Cyber Security Services Providers are a team of IT security experts with a wealth of experience spanning multiple technology domains and industries. We apply our cybersecurity consulting services and extensive knowledge of security best practices and standards to ensure that our clients’ mission-critical systems are reliably protected from all known and emerging threats. With our cybersecurity consulting services, we help our clients stay safe and ready for the digitalized future.

Software-level security
Security features are integral to all solutions we deliver. We also deploy available security updates to the software in place and deliver custom security enhancements.

Network monitoring
We set up 24/7 network monitoring to ensure permanent control over network elements (servers, firewalls, routers, switches, etc.) and keep an eye on their safe operation and integrity.

Infrastructure protection
Our team sets up security solutions and practices to shield enterprises’ IT infrastructures, including hardware and software assets, from potential cyber attacks.
Our Symantec Cyber Security Services
The Security Center of Excellence was formed to strengthen BitsByteSoft position as a cybersecurity consulting company. We offer our cybersecurity advisory & consulting services as a response to the rapidly growing number of security-related requests and the rising concern about the lack of intrinsic security in many enterprise-grade systems working with sensitive financial, medical, and private data. Today, this unit is involved in the majority of the company’s production processes, but also acts as a standalone department offering a wide range of services to our clients that choose BitsByteSoft among so many cybersecurity consulting companies.

Security assessment
We test embedded code, applications, networks, and hardware components for vulnerabilities. We conduct security assessment using various methods and at all levels: from penetration testing of web services and mobile apps to fuzz testing and reverse engineering of on-prem applications

Compliance audit
We analyze our clients’ IT landscape and check it for compliance with the most important industrial security standards, such as ISO 27001, NIST 80-53, HIPA, GDPR, and CCPA. We have devised an end-to-end approach for compliance checks to ensure the highest level of accuracy and predictability of results

Configuration/system audit
We perform full-scale penetration testing of isolated computer systems or entire networks. We identify issues in system configuration files, Active Directory settings, network permissions, database security, and key elements of a company’s IT infrastructure

SDLC compliance
The most secure systems are typically built in strict compliance with the SDLC process, where adequate time and effort is allocated to testing and quality assurance at each production stage. We help companies adjust their development processes to focus more on quality and intrinsic security

Security awareness
We help companies raise security awareness among developers, testers, and end users by highlighting the most important security-related aspects of their work. Our cybersecurity advisory & consulting services include how-to’s for every role involved in the day-to-day operation of IT systems of all types
Business continuity planning
Today’s companies can’t survive without a business continuity plan in case of emergencies. As a cybersecurity consulting company, we help our clients achieve their goals by expertly assessing their readiness for crisis situations and proposing disaster recovery guidelines

Long-term risk mitigation
We help companies address security concerns even before the start of a software development project by assessing its overall architecture. BitsByteSoft cybersecurity consulting means that we help reduce the cost of incidents, minimize downtime, and facilitate long-term product maintenance
Cyber security consulting: 3 levels
We understand that implementing specific security features is only right when they fall in line with the overall organizational security policy. When companies aren’t sure about measures they need, BitsByteSoft offers its cyber security consulting services as essential for establishing effective security practices.

Assessment
Working with corporate IT ecosystems, we evaluate the security posture to reveal its strengths and weaknesses, as well as check if it complies with regional and global security standards.

Strategy
We help businesses document their security roadmaps with imperative steps for achieving required cyber security levels through personalized methodologies and security solutions.

Training
Upon request, we carry out security training for IT professionals and business users. We explain how to manage security solutions and establish secure working practices for different devices.


Security pre-audit assistance
We are a cyber security consulting company that provides advisory services to companies preparing for certifications and compliance checks as part of a comprehensive security audit. We carry out all-round security assessments across an enterprise’s documented security practices and security solutions in place. We also help fill the revealed security gaps and improve security across all the domains


Security policies
Documented IT assets
Incident response programs
Data protection policies
Security training materials


Application security
Network analytics
Infrastructure protection
Physical security
Endpoint security
Cyber security testing
With its dedicated testing center, BitsByteSoft supports businesses ready to take a close look at their cyber security status. We thoroughly examine solutions, networks, and infrastructures to discover unseen vulnerabilities and security gaps that could be leveraged by malicious external and internal users. Our post-testing action plan includes countermeasures for patching revealed security loopholes and improving the overall state of the tested systems.
Vulnerability assessment
We deliver vulnerability assessment services to review corporate security objectively. Using a variety of vulnerability scanners, we scrutinize our customers’ environments and solutions to discover unpatched vulnerabilities that can attract hackers and leave a loophole to corporate assets and sensitive data.
Security code review
Our security engineers look into applications to inspect their security at the code level. The key goal of such code reviews is to make sure that the code doesn’t contain errors and that security controls are implemented correctly and operate as intended. By verifying every line of code, we ensure that applications have no blind spots and can withstand attacks.

Investigate
We analyze the systems to be tested, identify their role in the environment as well as key parameters and required configurations.

Benchmark
We examine requirements of the tested systems’ normal behavior and expected reactions in response to a cyberattack.

Scan
Based on the compliance guidelines and the customer’s business context, we configure and launch vulnerability scanners.

Report
We report on the discovered vulnerabilities and their potential impact on company-wide security in detail.

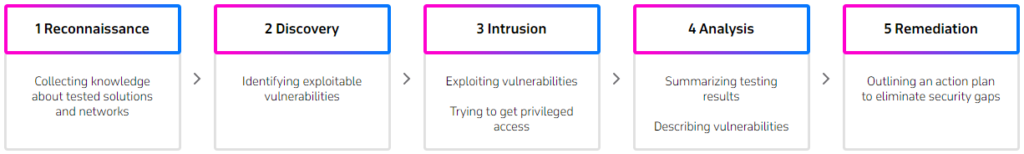
Penetration testing
BitsByteSoft ethical hackers perform penetration testing to examine app and network behavior in scenarios close to real-life cyberattacks. Relying on the proven OWASP and PTES methodologies, our team carries out white-, grey- and black-box penetration testing by simulating internal or external intruders’ actions and trying to exploit existing vulnerabilities.
The testing results in a detailed report with a full list of detected vulnerabilities classified by their nature and severity. The list is extended with effective measures for patching the vulnerabilities and restoring security of the tested systems.


Cloud security
Delivering cloud solutions for businesses globally, we put our effort into ensuring they are attack-resistant. Our cyber security consultants help businesses deploy protected cloud environments that support impregnable business workflows, enterprise collaboration, content and data management.

Secure cloud architecture
We design secure cloud architectures across different deployment models (public, private, hybrid, multicloud). Using cloud best practices, we ensure protection of network components, endpoints, and connections within cloud environments.

Cloud data protection
We mitigate security-related risks of cloud data storage, exchange and governance. Data loss prevention, encryption, data access management, and data monitoring are at the center of our data security services.

Identity management
Following the organizational hierarchy and security requirements, we build user taxonomies, define user permissions and access rights. We also handle user authentication issues within cloud apps and set up user metrics within cloud monitoring solutions.
Compliance
We hold ISO/IEC 27001 and ISO 9001 certifications, which guarantees the highest information security during our software development projects. We also help our customers from various business domains to align their IT ecosystems with the industry-specific regulatory compliance (PSI DSS, SOX, FISMA, GLBA, HIPAA, HITECH, etc.). Our testing services are the right choice for businesses that want to make sure their solutions meet the global standards of data and business process management. At the same time, our informed recommendations form a solid basis for companies to improve their security practices overall and the protection of certain apps and network components in particular.

Cooperation models
To start your cooperation with BitsByteSoft , you can choose the opton that fits your security goals and budget best.

On-demand security consulting
We are open to on-demand security assistance to help you resolve security issues of various origins and restore the normal operation of your IT environment. Our team delivers security enhancements and fine-tunes security solutions, as well as helps pass security testing and certifications.

Managed IT security services
When you don’t have internal computing and human resources to manage your IT ecosystem, you can delegate this demanding task to BitsByteSoft. Through our managed IT security services, we ensure ongoing monitoring and optimization of your enterprise security posture.
Benefits of our cybersecurity advisory & consulting services
Long-term risk mitigation
Cybersecurity consulting services from BitsByteSoft keep our clients protected from intrusion attempts, data leaks, identity theft, and other threats that can jeopardize the work of a company in the long run.

BitsByteSoft helps maintain security to produce a long-term risk mitigation plan and revisiting it on a regular basis. From security patches and process optimization to on-site security training — we’ve got it all covered within the scope of our cybersecurity consulting services. Our holistic approach to data security and cybersecurity consulting gives our clients the much-needed confidence in a successful tomorrow.
Regular security audits
Our managed security services enable any organization concerned with the protection of their own and their clients’ data and systems to keep IT security at a consistently high level.

This can be achieved through regular security audits at all levels. We stand out among cybersecurity consulting companies, because our specialists ensure that any changes to the system are fully in line with established security policies and guidelines. Whenever a particular security standard is modified, we help evaluate the system-wide impact of this change and update the affected components.
Compliance at all levels
Our cybersecurity consulting services not only help identify and apply the best tools and methods for data protection, but also ensure maximum compliance with the most stringent security standards.

As a cybersecurity consulting company, we scrupulously analyze our clients’ systems, assess them from various standpoints, perform penetration testing, and document the results in great detail. These conclusions can then be used for adapting the systems to existing or future security standards to ensure their stable operation. Our cybersecurity consulting allows companies reach global standards of cyber resilience.
Industries we serve

Automotive
Process large volumes of data generated by connected cars, as well as integrate in-vehicle apps with cloud automotive services

FinTech
Take advantage of intelligent approaches to supervising financial services and affordable flexibility offered by cloud computing

Retail
Unify data across the supply chain and leverage advanced cloud capabilities, such as AI and Big Data, to drive maximum value for customers

Agriculture
Leverage the power of cloud to get accurate prediction on products that are in demand by different markets and adjust production respectively

Real Estate
Improve occupants’ experience and manage spaces more effectively with cloud-based analytics powered by ML algorithms

Transportation
Bring multiple pieces of data together to accelerate the shift to smarter fleet management, as well as enhance transportation and logistics services

Telecom
Migrate to a cloud-based network architecture and implement cloud-native approach to extend your offering with next-gen digital services

Healthcare
We’re driving digital transformation in national healthcare by developing medical apps for doctors and patients to facilitate their interactions
Customer Success Stories

Drone Data Platform for Safe and Regulated Flights
We helped to create software for drones to pursue a safe and collaborative future for regulated drone flights

IoT Solution for a Smart Building Ecosystem
We helped deliver a smart building solution that relies on extensive IoT functionality and connected sensors

Smart Connectivity to Redefine Consumers Behavior
We helped reinvent the everyday consumption of goods that our client provides to 150 million consumers worldwide

Real-Time Advertising Platform
We are helping make a mobile-first ad exchange platform the number-one marketplace for world’s biggest advertisers and publishers

Security Assessment of a Car Head Unit
We offered a proven solution to enhance the safety and digital security of high-tech cars

Cost-Effective 3D Object Detection for Autonomous Vehicles
We used stereovision and mathematical algorithms to simulate Lidar signals without compromising quality

Data-Driven Protocols for Advanced Driver Assistance Systems
We helped equip German premium cars with the most advanced driver assistance functions on the market

3D Mapping Solutions for Data Visualization
We’re helping the world’s top location expert build comprehensive 3D mapping solutions for data visualization

High-End Concept Design for Connected Car-Sharing Solution
We have designed an innovative human machine interface (HMI) application to bring the connected car-sharing customer experience to a new…

ANPR-based Automated Payment Solution as a Compelling Differentiator for Brands
We’ve developed a contactless automated payment system that can give a competitive edge to merchants and service providers

Pedestrian Tracking & Collision Prediction to Enhance Mobility Safety
We’ve developed software for detecting pedestrians and predicting their trajectories by leveraging the potential of Kalman filtering

Data Analytics Platform for Sales and Marketing Insights
We’re developing a big data analytics platform to help a global tire producer activate sales opportunities by discovering regional potential

Employee Management Software for Enhanced Telecom Workplace Services
We’re building all-in-one employee management software to create exceptional workplace experiences in handling daily routines

Smart Facility & Energy Management System Software
We developed a software suite for a facility, energy, and workplace management system

Microservice Architecture to Optimize Supply Chain Management and Logistics
We’re helping one of the world’s top tire manufacturers get through digital transformation with a sophisticated microservice platform

Logistics System to Orchestrate Product Management Processes
We’re developing a fully fledged backend middleware platform to streamline logistics operations and supply chain management

DevOps for Enterprises Services to Ensure Secure Platform Development Environment
We’ve applied DevOps for enterprises platform design and development solution for a Fortune 500 retailer Key features

Big Data for Retailers: A Platform for Equipment Monitoring in Supply Chains
We’ve developed a real-time big data analytics and temperature monitoring platform for a network of 125 stores in the Baltic…
Frequently Asked Questions about Cyber Security Design Services
What is your pricing for custom programming services?
BitsByteSoft provides flexible and adjustable pricing models for our custom programming services, with the option to combine different engagement models for specific services within the same project. Every engagement is unique, and estimates for the cost of custom application development services may vary depending on the complexity of the project and your desired involvement in the management of the development team.
What does your model of cooperation for custom-built software development look like?
At BitsByteSoft, we work with custom programming projects of any size, scale, and complexity. We pick the cooperation model that’s most suitable depending on a client’s previous experience and needs as well as the project’s complexity: dedicated development team, managed delivery, or product development. Each of these models covers a different set of needs and entails a different way in which our experts engage in developing custom-built software — performing exclusively engineering tasks; managing a full range of engineering projects, supervised teams, or programs; or developing a holistic product from the initial idea stage through bringing it to the market.
Can you describe your remote communication process while delivering custom application development services?
BitsByteSoft will establish a successful framework for remote communication between your in-house team and your remote BitsByteSoft team at the start of your custom application development project. In order to allocate a sufficient amount of time for initial team alignment and knowledge transfer, the BitsByteSoft team will adjust its work schedule to achieve a better time overlap. We will communicate with the tools you prefer to use with a custom application development company.
How does BitsByteSoft enhance the professional development of its employees?
As a leading custom application development company, we pay attention to the continuous growth of our employees and their job satisfaction. We’ve established a Professional Development Department whose responsibility is to provide high-quality education for BitsByteSoft employees. All employees have their own Personal Development Plans (PDPs) based on which they attend professional internal trainings as well as online and offline external courses, conferences, and workshops.

Let’s work together on your
next project
Drop us a line about your project at contact@bitsbytesoft.com or via the contact form below with attachments, and we will contact you within a business day.







